Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.
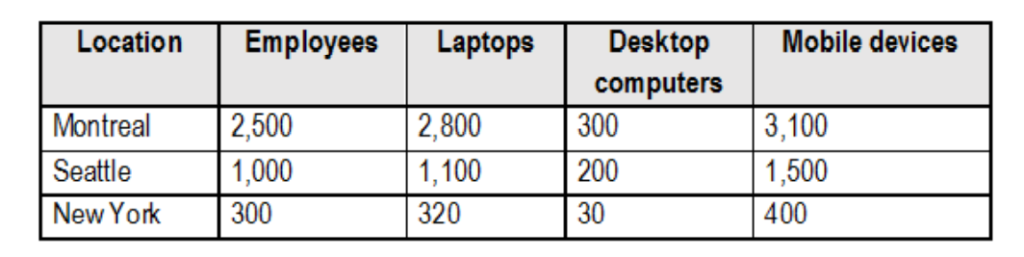
The company has the offices shown in the following table.
Contoso has IT, human resources (HR), legal, marketing, and finance departments. Contoso uses Microsoft 365.
Existing Environment
Infrastructure
The network contains an Active Directory domain named contoso.com that is synced to a Microsoft Azure Active Directory (Azure AD) tenant. Password writeback is enabled.
The domain contains servers that run Windows Server 2016. The domain contains laptops and desktop computers that run Windows 10 Enterprise.
Each client computer has a single volume.
Each office connects to the Internet by using a NAT device. The offices have the IP addresses shown in the following table.
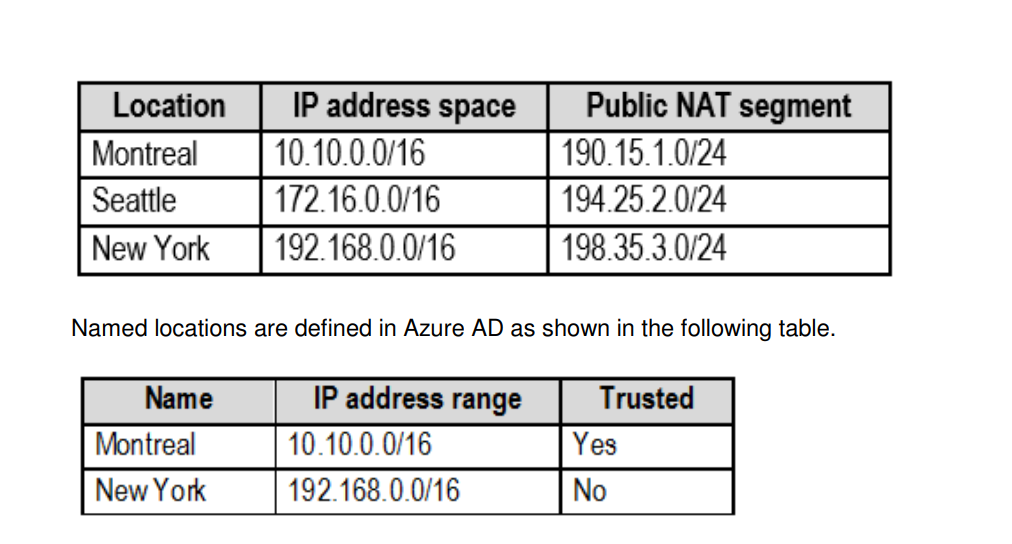
From the Multi-Factor Authentication page, an address space of 198.35.3.0/24 is defined in the trusted IPs list.
Azure Multi-Factor Authentication (MFA) is enabled for the users in the finance department.
The tenant contains the users shown in the following table
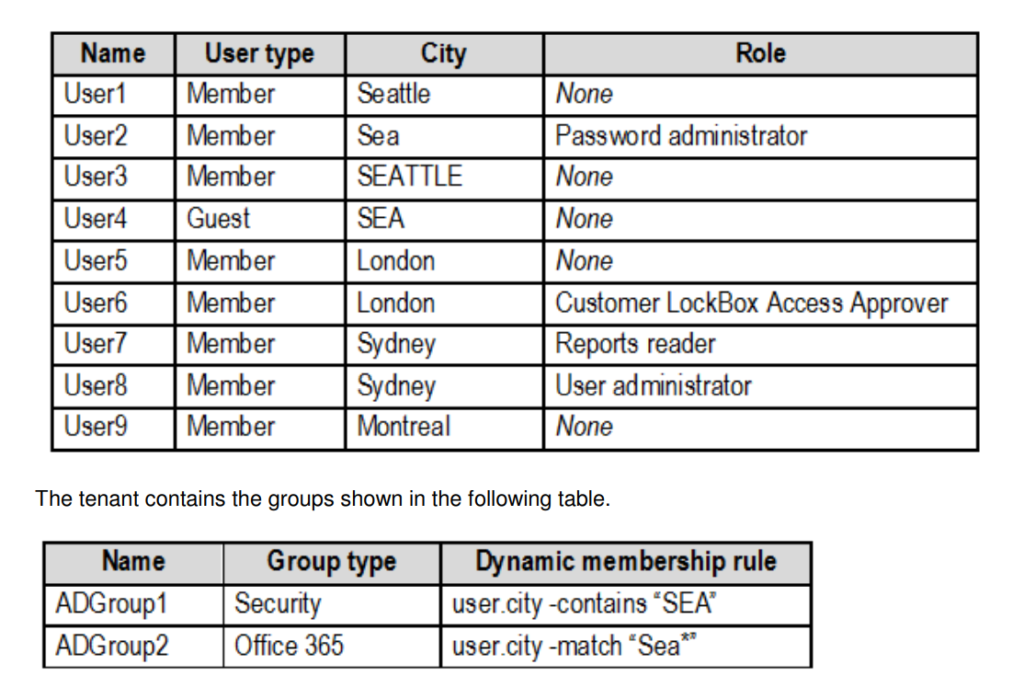
Customer Lockbox is enabled in Microsoft 365.
Microsoft Endpoint Manager Configuration
The devices enrolled in Microsoft Endpoint Manager are configured as shown in the following table
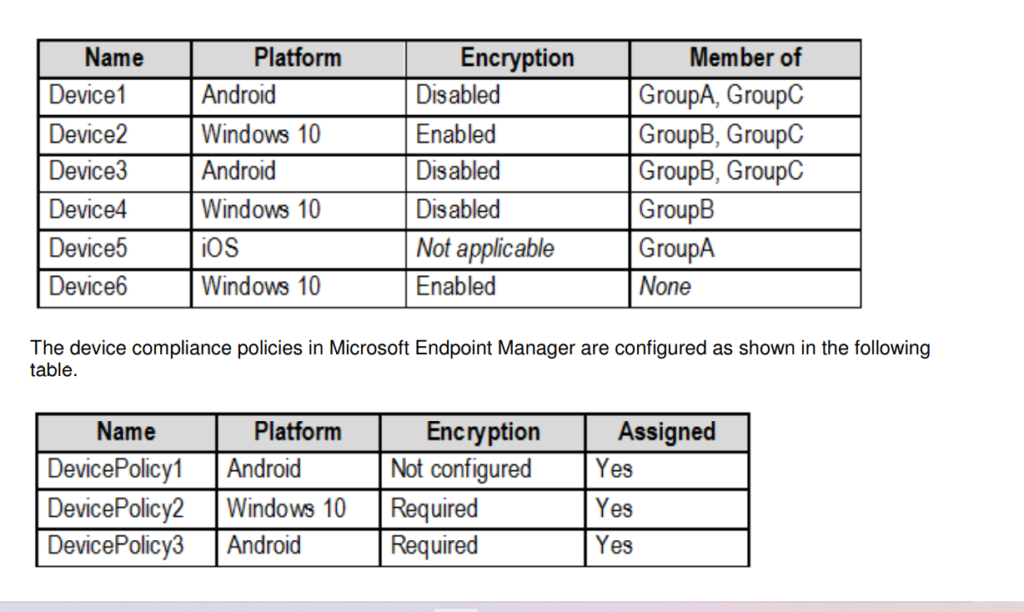
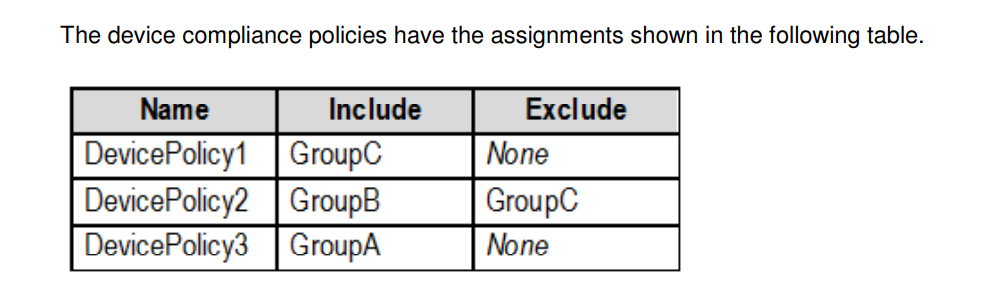
The Mark devices with no compliance policy assigned as the setting are set to Compliant.
Requirements
Technical Requirements
Contoso identifies the following technical requirements:
Use the principle of least privilege
Enable User1 to assign the Reports reader role to users
Ensure that User6 approves Customer Lockbox requests as quickly as possible
Ensure that User9 can enable and configure Azure AD Privileged Identity Management