Microsoft Security Administration(MS-500) Case Study-4
Overview
You have a Microsoft 365 E5 subscription that uses Microsoft Endpoint Manager.
The Compliance policy settings are configured as shown in the following exhibit.
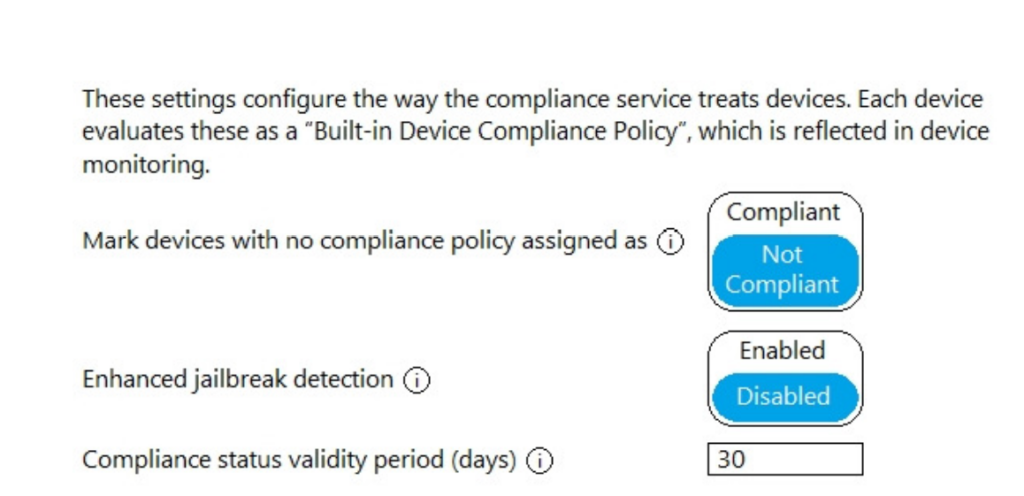
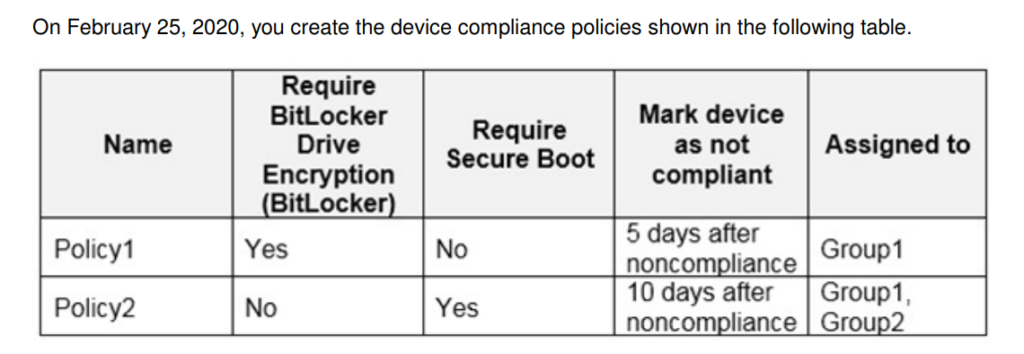
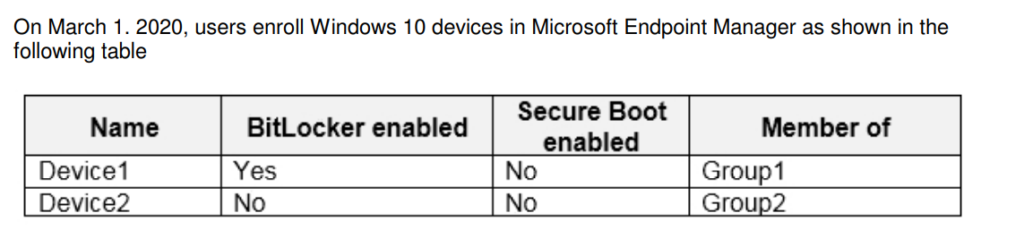
You have a Microsoft 365 E5 subscription that uses Microsoft Endpoint Manager.
The Compliance policy settings are configured as shown in the following exhibit.



You must be aware your computer has two different IP addresses that must be the reason you clicked on this blog to learn more about them. Well if you didn’t know it earlier, it doesn’t matter we will tell you about it. So, let’s start by telling you that there are two types of IP…
Overview Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.The company has the offices shown in the following table. Contoso has IT, human resources (HR), legal, marketing, and finance departments. Contoso uses Microsoft 365. Existing Environment Infrastructure The network contains an Active…

Are you ready to become a certified Microsoft 365 Administrator in 2025? Our MS-102 Practice Exams are here to help you achieve your certification goals with confidence! Designed by experts, these exams cover real-world scenarios and the latest Microsoft 365 updates to ensure you’re fully prepared. With our practice exams, you’ll get: • Up-to-date content…
Overview You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com. Four Windows 10 devices are joined to the tenant as shown in the following table. On which devices can you use BitLocker To Go and on which devices can you turn on auto-unlock? To the answer, select the appropriate options in the…
Overview Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattleand New York.The company has the offices shown in the following table. Contoso has IT, human resources (HR), legal, marketing, and finance departments. Contoso usesMicrosoft 365. Existing Environment Infrastructure The network contains an Active Directory domain…

Malware is a broader term used in the computer field for most unwanted malicious software. This software’ may get installed onto your computers with or without your permission and can harm your computer system or steal your confidential information in some way. We will discuss few terminologies used in the computer field to describe this…
When I initially left a comment I seem to have clicked on the -Notify me when new comments are added- checkbox and from now on every time a comment is added I recieve four emails with the exact same comment. Perhaps there is a means you can remove me from that service? Kudos!
I would like to thank you for the efforts youve put in penning this website. I really hope to check out the same high-grade content by you later on as well. In truth, your creative writing abilities has encouraged me to get my very own website now 😉
Itís nearly impossible to find educated people in this particular subject, however, you seem like you know what youíre talking about! Thanks