Microsoft Security Administration(MS-500) Case Study-4
Overview
You have a Microsoft 365 E5 subscription that uses Microsoft Endpoint Manager.
The Compliance policy settings are configured as shown in the following exhibit.
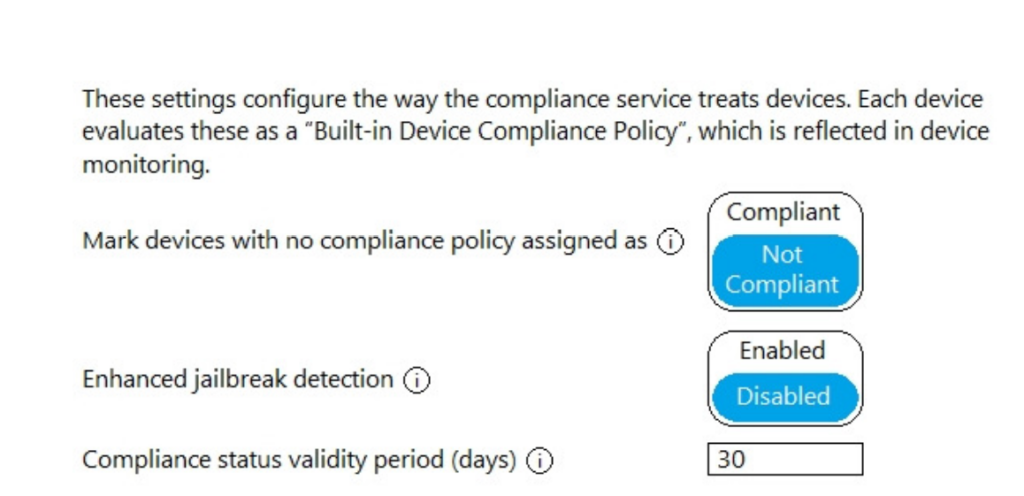
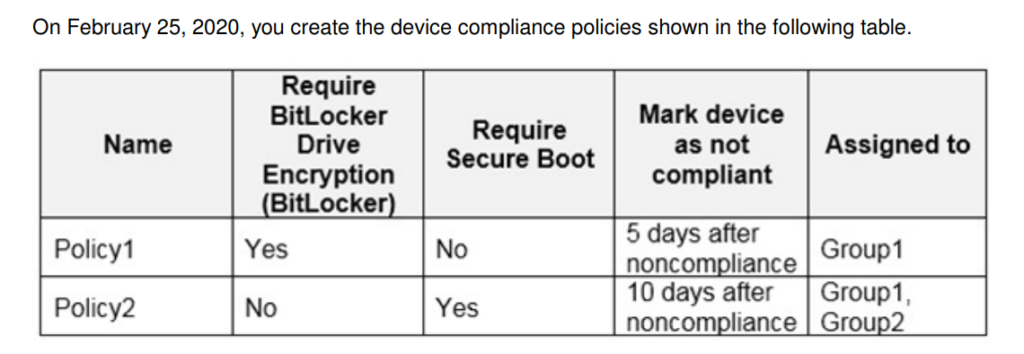
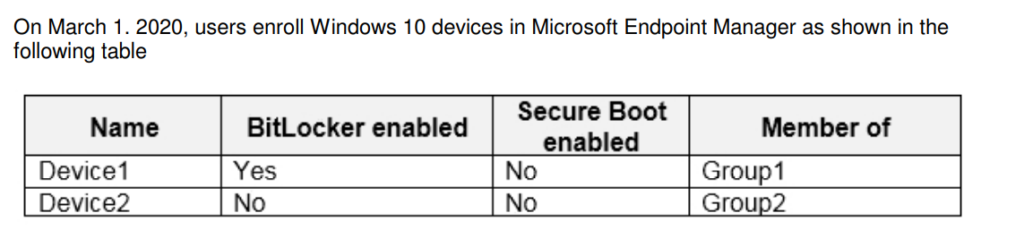
You have a Microsoft 365 E5 subscription that uses Microsoft Endpoint Manager.
The Compliance policy settings are configured as shown in the following exhibit.



So, you think your IP Address is not known to the public on the internet, you are not quite 100% correct. There are ways people on the internet and people who intend to do so can capture your IP address if they have some technical knowledge. Your Internet Service Provider is not the only one…

Copilot Notebook interface screenshot – Microsoft 365 AI workspace”
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shownin the following table. Quiz For each of the following statements in the quiz, select Yes if the statement is true. Otherwise, select No.
Overview Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.The company has the offices shown in the following table. Contoso has IT, human resources (HR), legal, marketing, and finance departments. Contoso uses Microsoft 365. Existing Environment Infrastructure The network contains an Active…

BYOD is an organizational policy abbreviated for “Bring Your Own Device”. Organizations that are in favor of BYOD policy allow their employees to bring their own mobile devices to their work and connect to IT infrastructure. At the same time, some companies think allowing personal devices to organizational networks and resources is a big risk….

The Researcher agent in Microsoft 365 Copilot is designed to help professionals gather information, explore topics, summarize complex content, and generate structured insights — all through natural language. Whether you’re preparing a report, analyzing trends, or drafting content, the Researcher agent accelerates your workflow by pulling together high‑quality, relevant information in seconds. In this post,…
When I initially left a comment I seem to have clicked on the -Notify me when new comments are added- checkbox and from now on every time a comment is added I recieve four emails with the exact same comment. Perhaps there is a means you can remove me from that service? Kudos!
I would like to thank you for the efforts youve put in penning this website. I really hope to check out the same high-grade content by you later on as well. In truth, your creative writing abilities has encouraged me to get my very own website now 😉
Itís nearly impossible to find educated people in this particular subject, however, you seem like you know what youíre talking about! Thanks